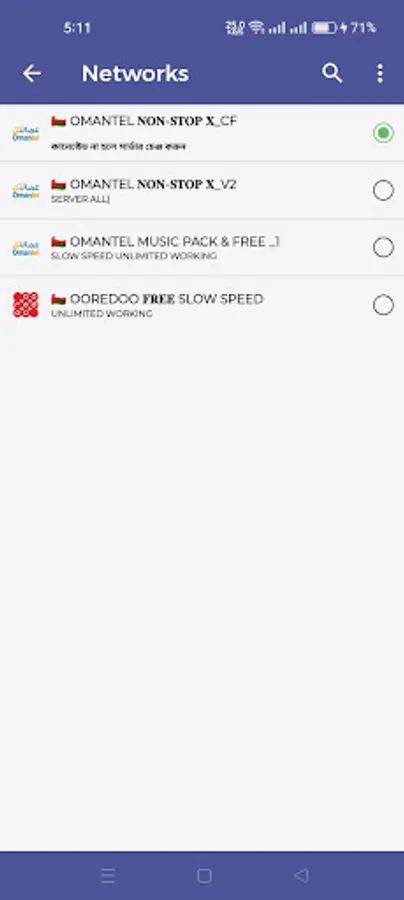
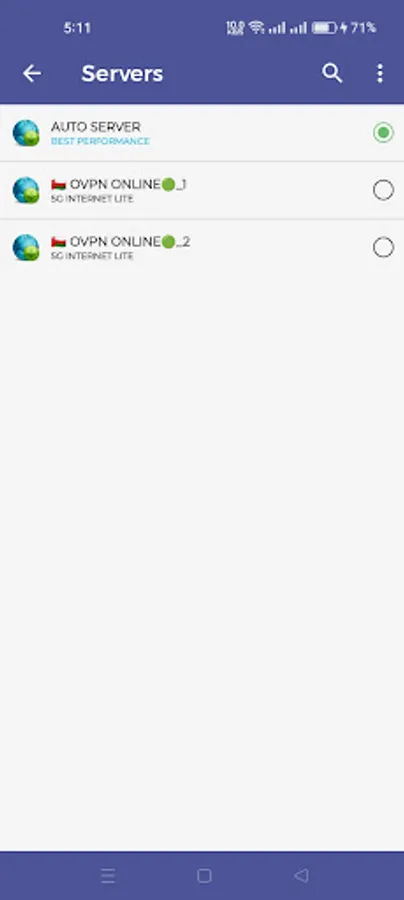
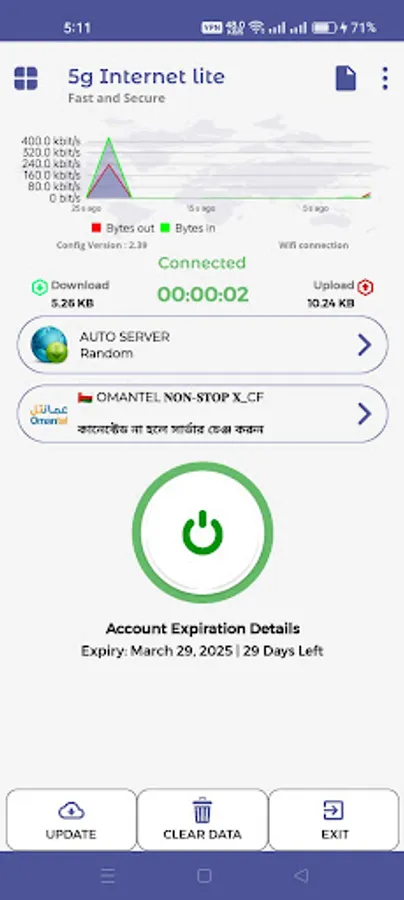
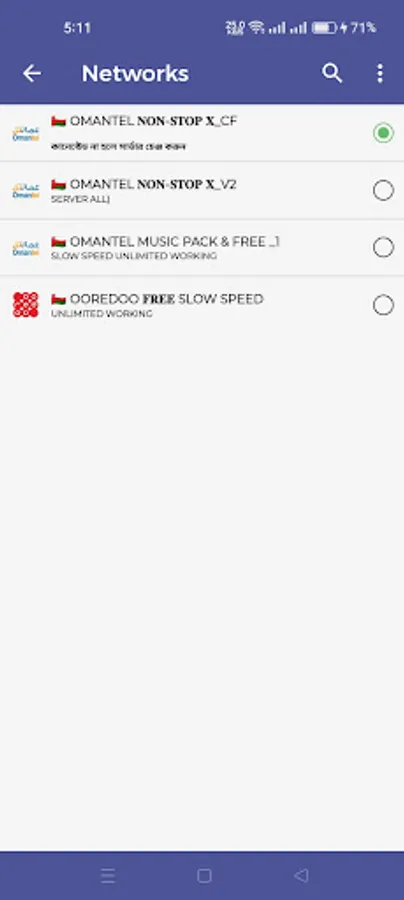
5G Internet Lite
XTreme Team
3.2 ★
store rating
10,000+
downloads
Free
AppRecs review analysis
AppRecs rating 2.5. Trustworthiness 76 out of 100. Review manipulation risk 36 out of 100. Based on a review sample analyzed.
★★☆☆☆
2.5
AppRecs Rating
Ratings breakdown
5 star
40%
4 star
20%
3 star
0%
2 star
0%
1 star
40%
What to know
✓
Credible reviews
76% trustworthiness score from analyzed reviews
⚠
Review quality concerns
82% of sampled 5-star reviews are very short
⚠
High negative review ratio
40% of sampled ratings are 1–2 stars
About 5G Internet Lite
5G Internet Lite VPN is a lightning-fast app provide free VPN service. the Internet securely and anonymously.
Why choose Eagle VPN?
✅ Works with Wi-Fi, 5G, LTE/4G, 3G and all mobile data carriers
✅ No usage and time limit
✅ No registration or configuration required
Download 5G Internet Lite VPN, the world's fastest secure virtual private network, and enjoy it all!
Hoping you suggestion and good rating to keep it growing and make it better :-)
VPN related introduction
A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running across the VPN may therefore benefit from the functionality, security, and management of the private network.
Individual Internet users may secure their transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers for the purpose of protecting personal identity and location. However, some Internet sites block access to known VPN technology to prevent the
VPNs cannot make online connections completely anonymous, but they can usually increase privacy and security. To prevent disclosure of private information, VPNs typically allow only authenticated remote access using tunneling protocols and encryption techniques.
Mobile virtual private networks are used in settings where an endpoint of the VPN is not fixed to a single IP address, but instead roams across various networks such as data networks from cellular carriers or between multiple Wi-Fi access points. Mobile VPNs have been widely used in public safety, where they give law enforcement officers access to mission-critical applications, such as computer-assisted dispatch and criminal databases, while they travel between different subnets of a mobile network..
Why choose Eagle VPN?
✅ Works with Wi-Fi, 5G, LTE/4G, 3G and all mobile data carriers
✅ No usage and time limit
✅ No registration or configuration required
Download 5G Internet Lite VPN, the world's fastest secure virtual private network, and enjoy it all!
Hoping you suggestion and good rating to keep it growing and make it better :-)
VPN related introduction
A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running across the VPN may therefore benefit from the functionality, security, and management of the private network.
Individual Internet users may secure their transactions with a VPN, to circumvent geo-restrictions and censorship, or to connect to proxy servers for the purpose of protecting personal identity and location. However, some Internet sites block access to known VPN technology to prevent the
VPNs cannot make online connections completely anonymous, but they can usually increase privacy and security. To prevent disclosure of private information, VPNs typically allow only authenticated remote access using tunneling protocols and encryption techniques.
Mobile virtual private networks are used in settings where an endpoint of the VPN is not fixed to a single IP address, but instead roams across various networks such as data networks from cellular carriers or between multiple Wi-Fi access points. Mobile VPNs have been widely used in public safety, where they give law enforcement officers access to mission-critical applications, such as computer-assisted dispatch and criminal databases, while they travel between different subnets of a mobile network..