AppRecs review analysis
AppRecs rating 4.3. Trustworthiness 0 out of 100. Review manipulation risk 0 out of 100. Based on a review sample analyzed.
★★★★☆
4.3
AppRecs Rating
Ratings breakdown
5 star
77%
4 star
8%
3 star
0%
2 star
0%
1 star
15%
What to know
✓
High user satisfaction
85% of sampled ratings are 4+ stars (4.3★ average)
About Cyber Manhunt
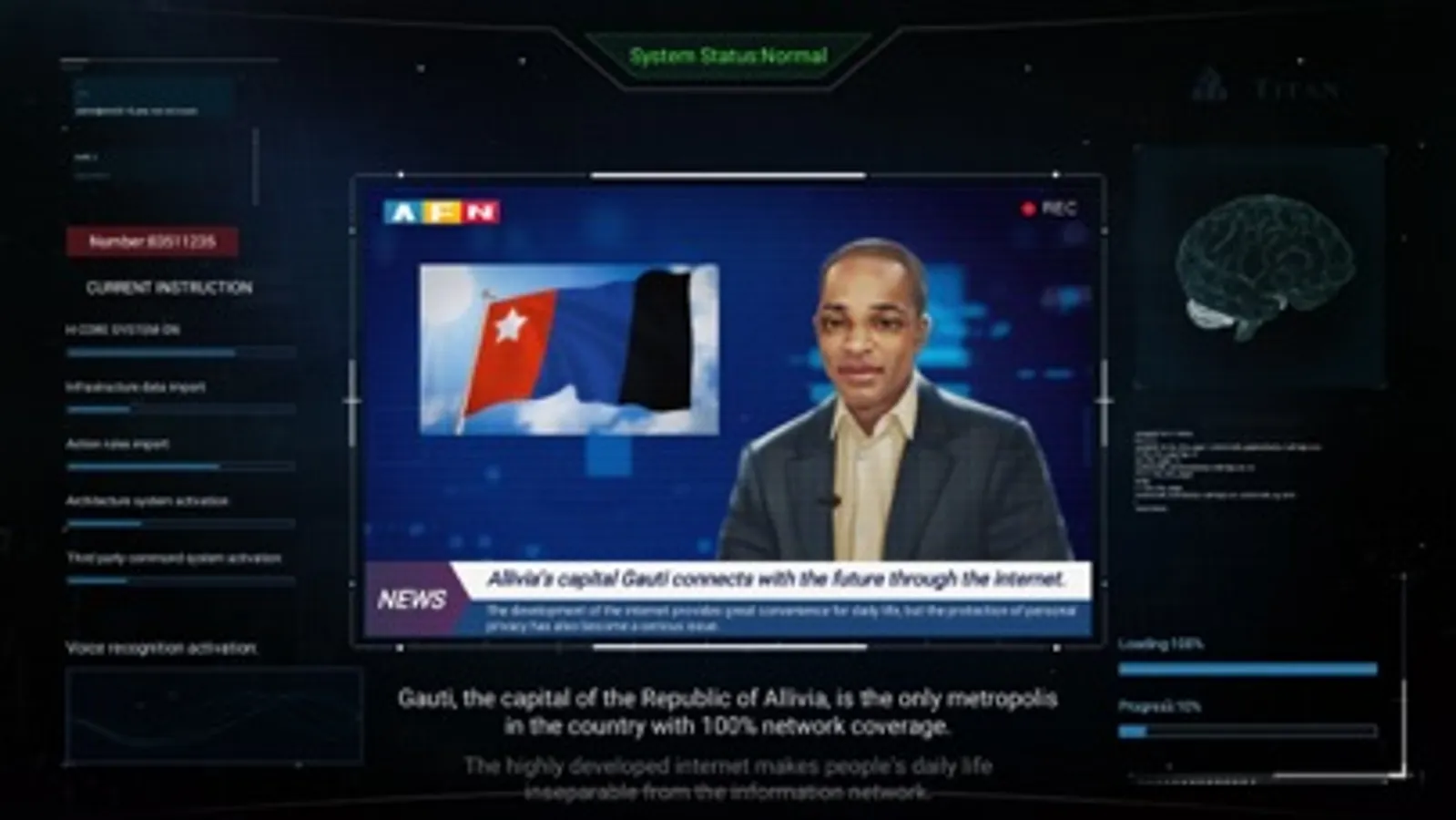
Cyber Manhunt is a Cyber-Style, Realistic- Society theme, Story-Rich indie game. The game taked place in the Republic of Alivia with some different theme stories ,but the fate of the characters is closely related in there. It will focus on social issues liking big data, hacking, citizen privacy etc...
We want to reveal the profound themes behind the stories with wonderful plots and gamification. And let players pay more attention to Cyber Violence and Privacy Breaches.
[Contents]
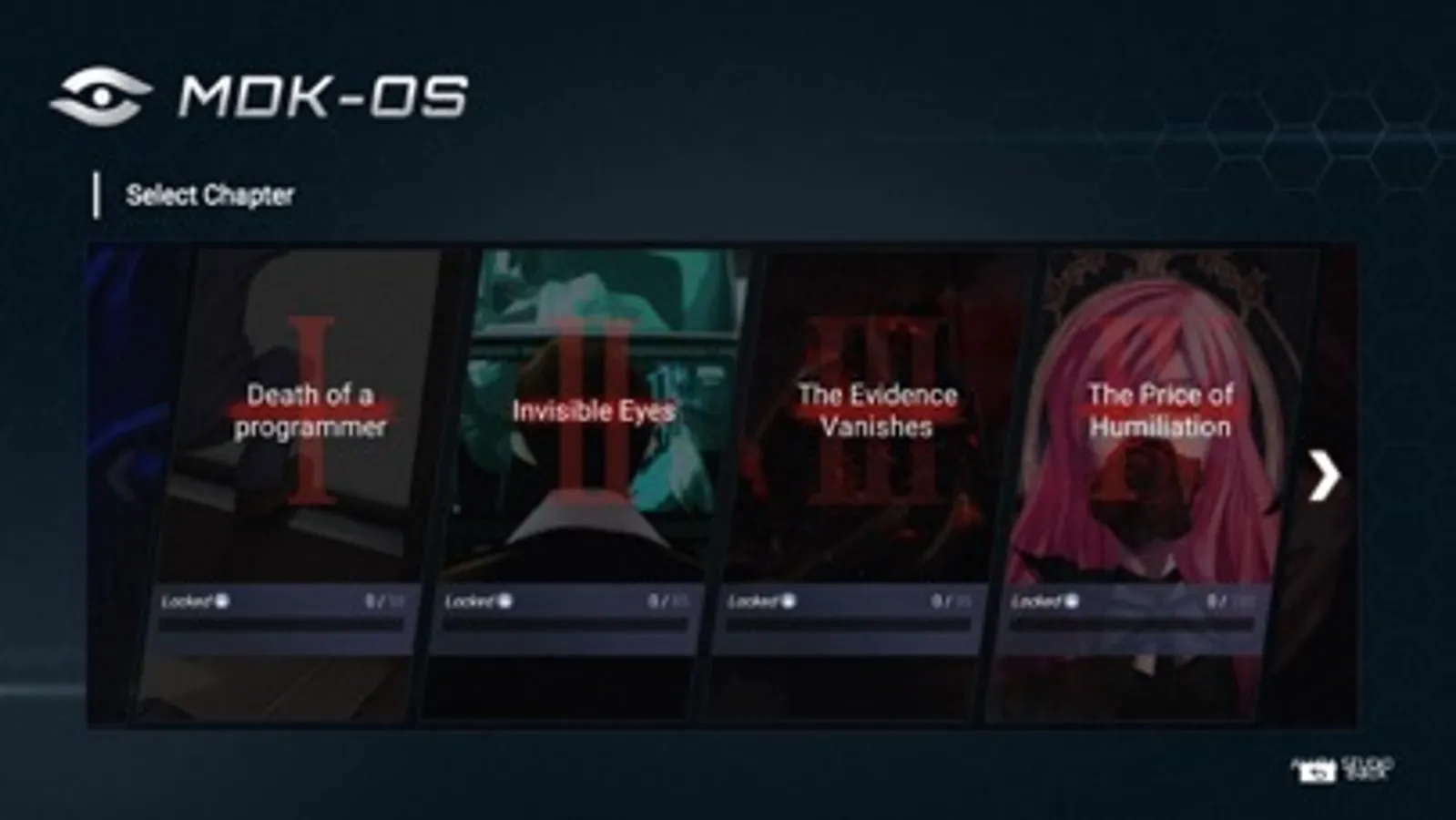
◆Chapter I: Death of a Programmer
The CEO of a company committed suicide by jumping off a building, and claimed that he was extorted tens of millions by his wife. While his wife posted photos of domestic violence on social networks. Who is lying?
◆Chapter II: Invisible Eyes
The indecent video of the female college student went viral on the Internet. At this moment, she was already socially dead. Who is the initiator? Who should protect the safety of women?
◆Chapter III: The Evidence Vanishes
The student council president, who is both excellent in character and study, suddenly disappeared. The bullying incident made the case more complicated. Who is the murderer and who is the victim?
◆Chapter IV: The Price of Humiliation
The female singer has been exposed again! Threatening letters, hype, the suicide of former girl group members... The Internet has set off a public opinion carnival again!
◆Chapter V: Immortal Code
When the society is in madness, are you willing to join the Immortal Code to obtain true love and immortality?
◆DLC: Home Sweet Home
Behind this seemingly sweet and happy family, everyone has their own secrets, what is the truth hidden behind?!
◆DLC: Hello World!
Senior researcher of Titan Dr. Lucrezia died in a terrible car accident on the spot, but the fellow Benjamin took escape from death. But he did not realize that he was about to be involved in a huge conspiracy…
[Features]
◆Highly Immersive: Gamers play as a hacker in the game, accepts the commission of the company, and solve dangerous incidents.
◆Rich Gameplay: There are lots of features of Social Engineering in the game, which is including Detecting, Tracking, Puzzles-Solving, Destroying and Hacking etc..
◆Wonderful Plots: Each chapter in the game will reflect a current hot social topic, such as: Sneak Shot, Cyber Violence, School Bullying, etc...
◆Multiple Roles: There are many different roles in this game with a flash of personality. Their stories would be dug by yourself.
◆Fully Dubbing: All the characters in the game have their own voice actors that make the game experience more immersive.
◆Original Music: There are some original songs in the game, and the lyrics and vocals are all completed by the studio.
[Gameplay]
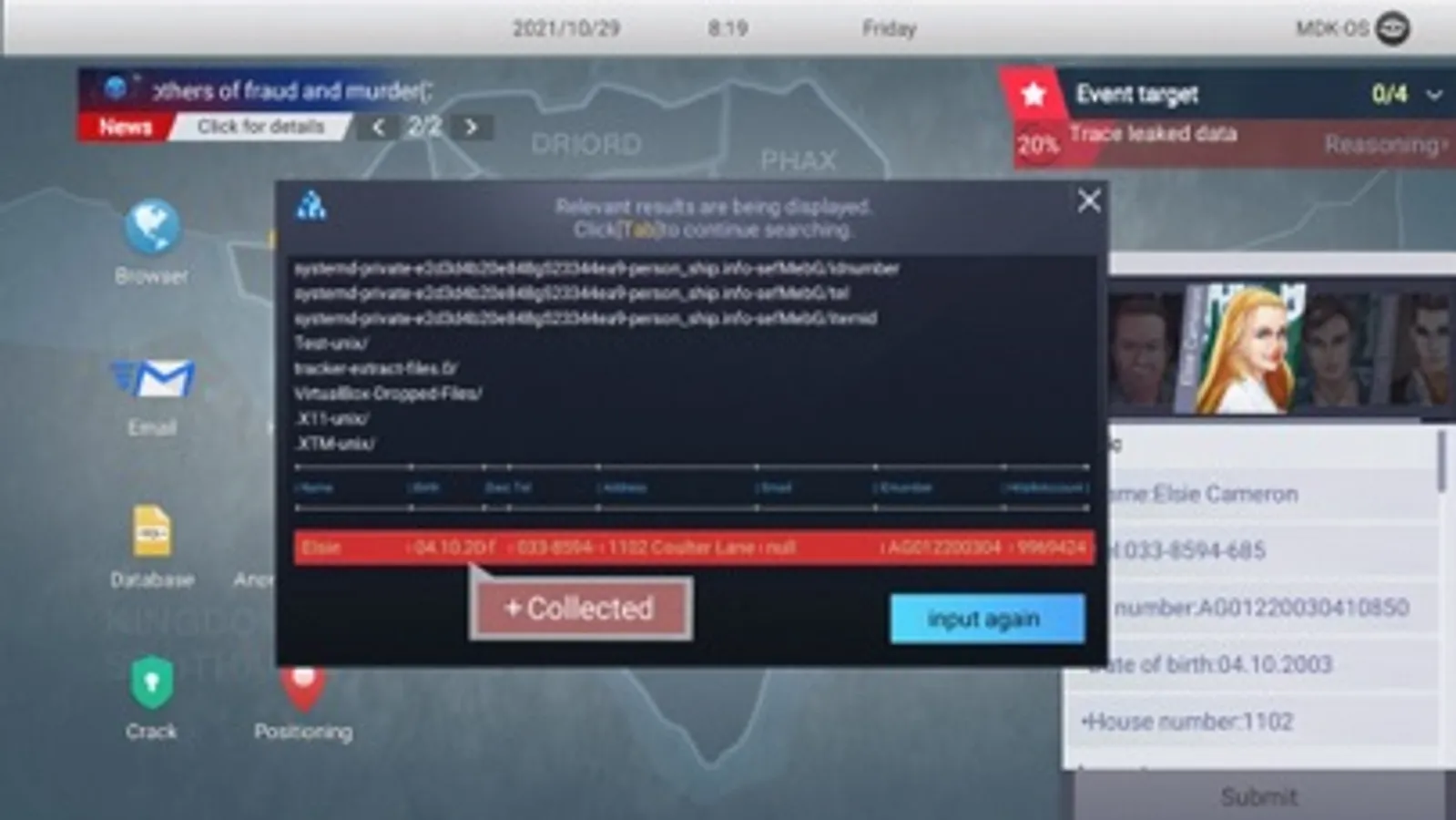
◆Web Search: You should collect basic information about the targets through the Internet search.
◆Database: You can use the database to get deep information about targets.
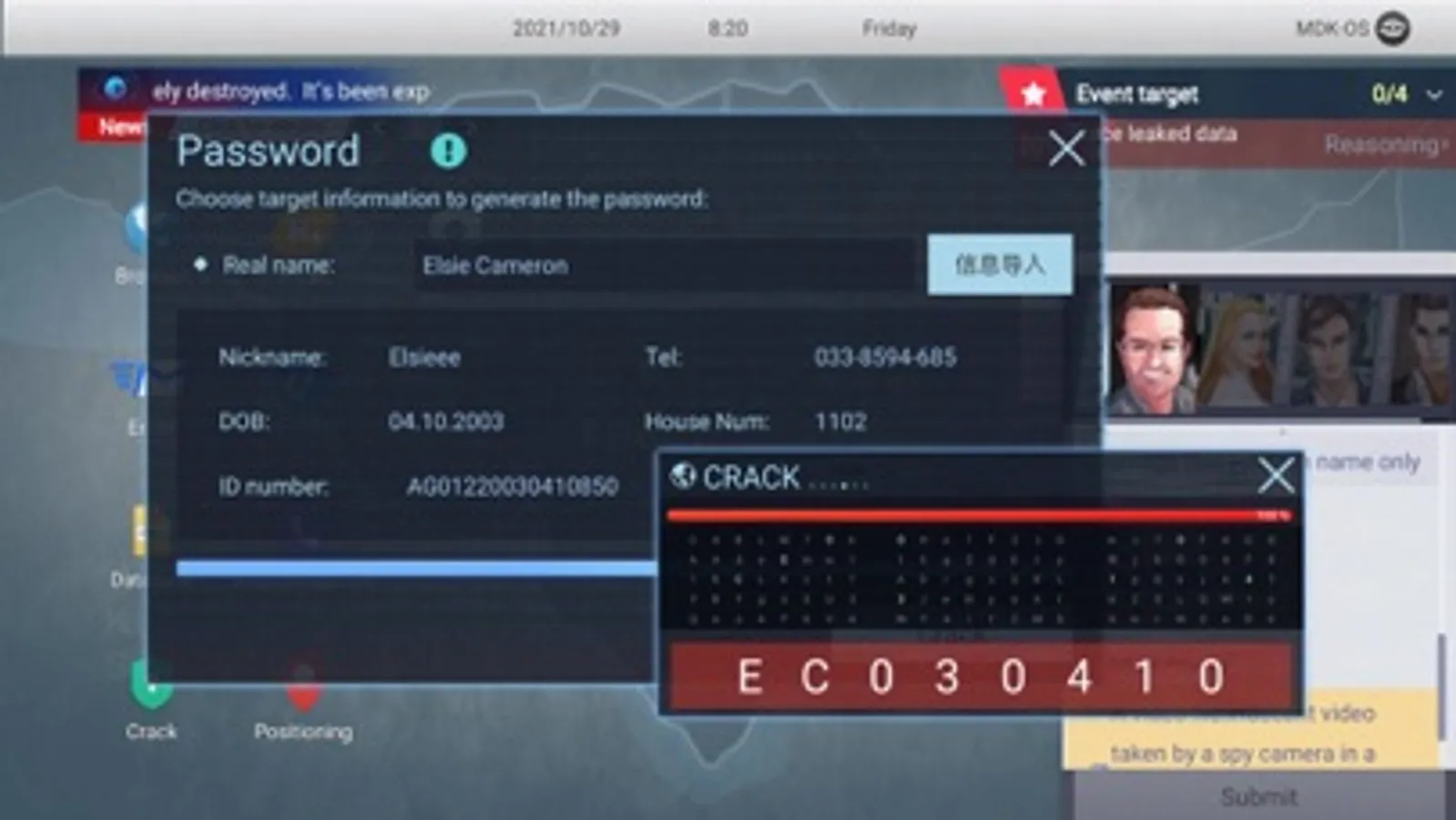
◆Crack: You would get passwords based on the obtained target's information, and use it to log in to accounts of different platforms.
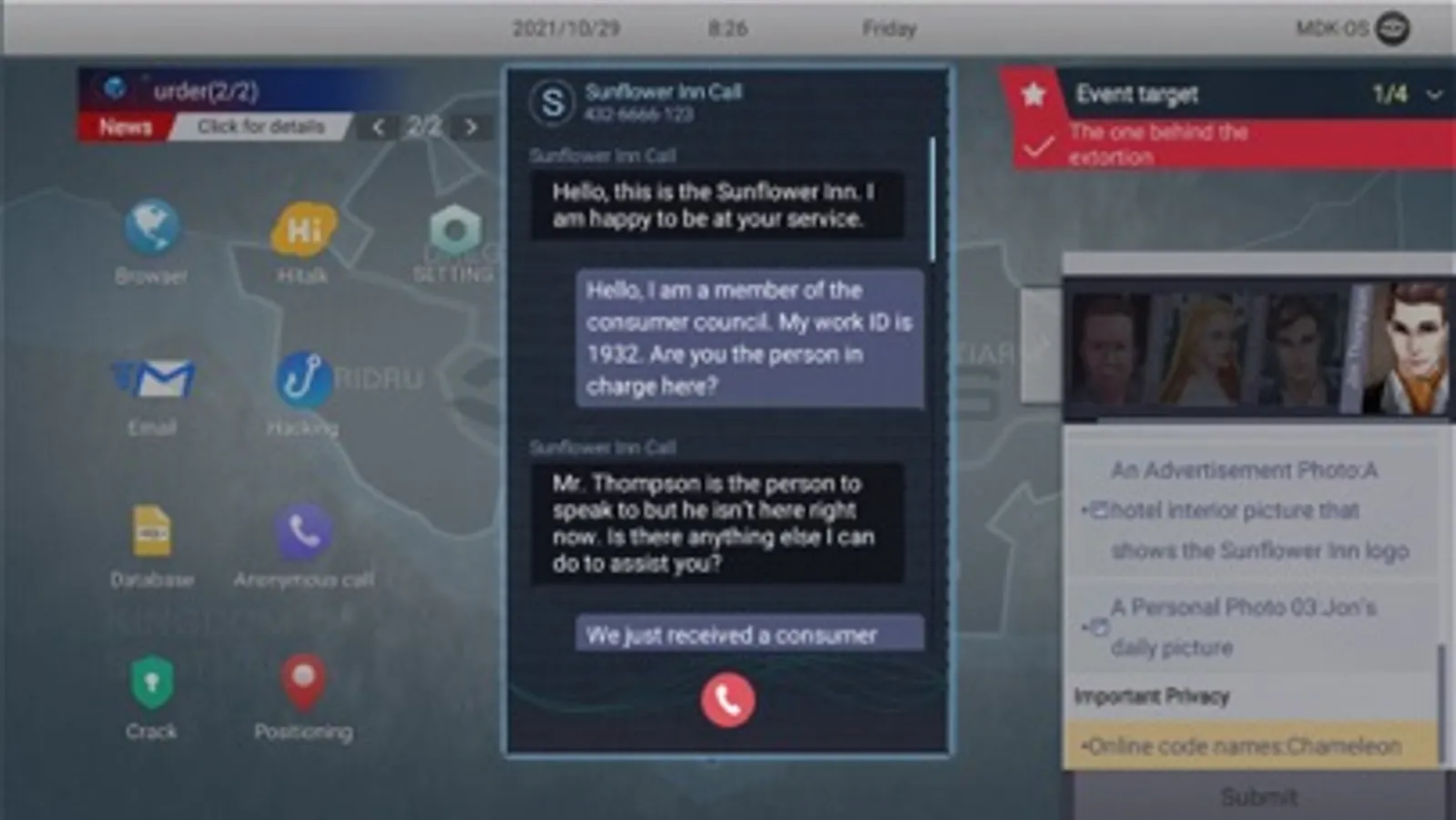
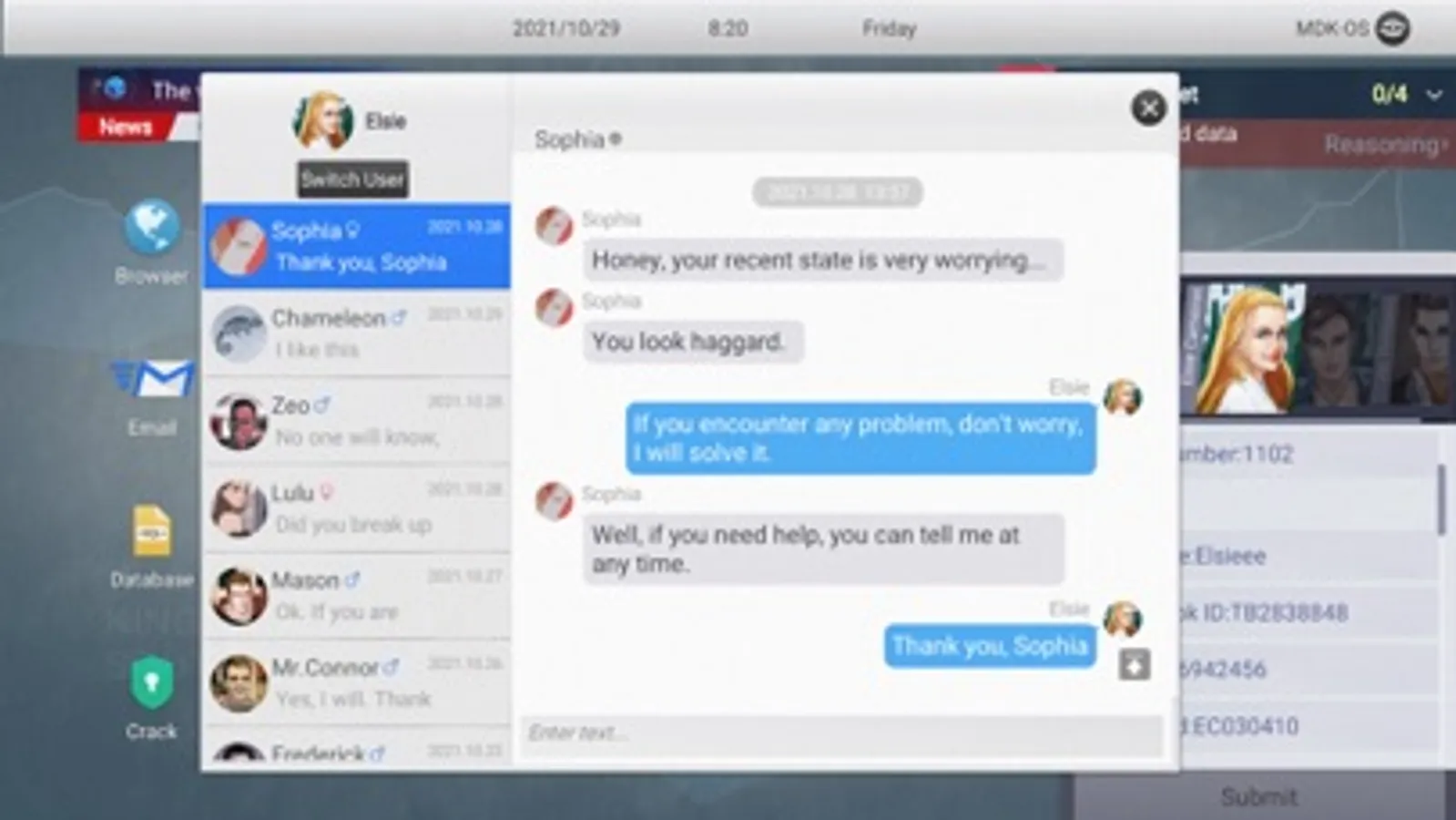
◆Chat: The exciting thing is that you need to chat with targets by disguise and use the information to get the trust of the target.
◆Phishing: You can send phishing links to hack the targets' hardware devices, and get private information.
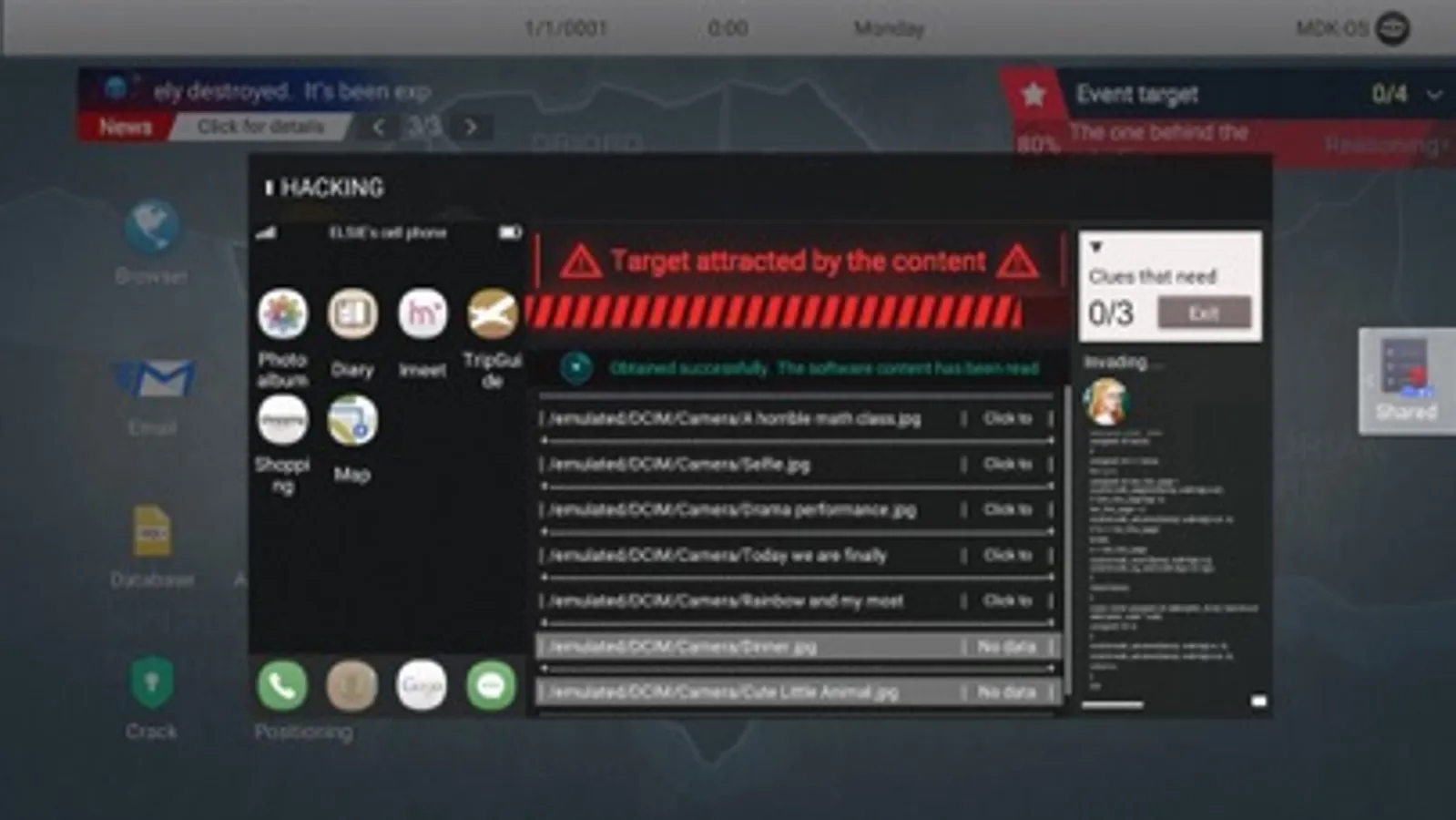
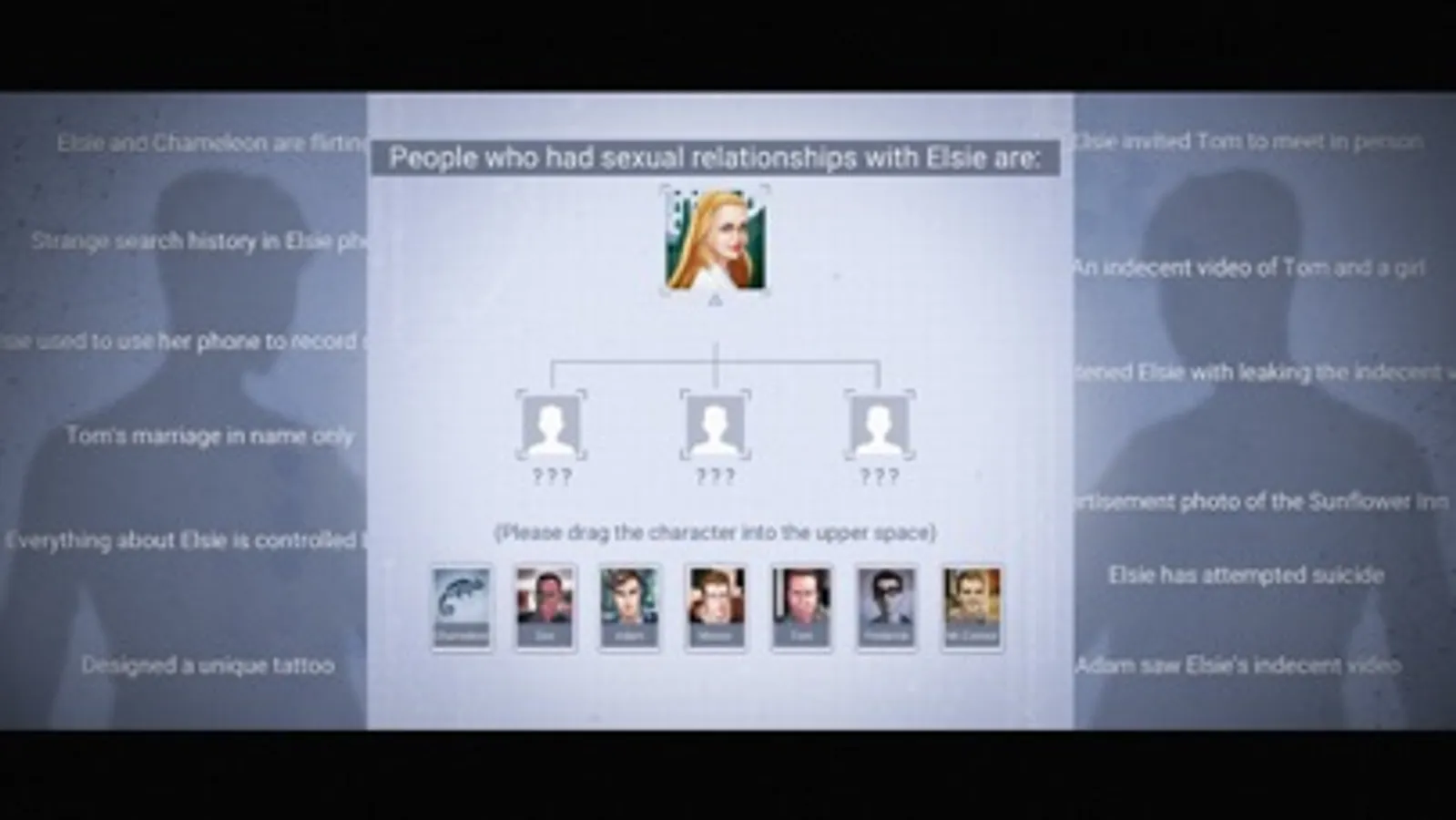
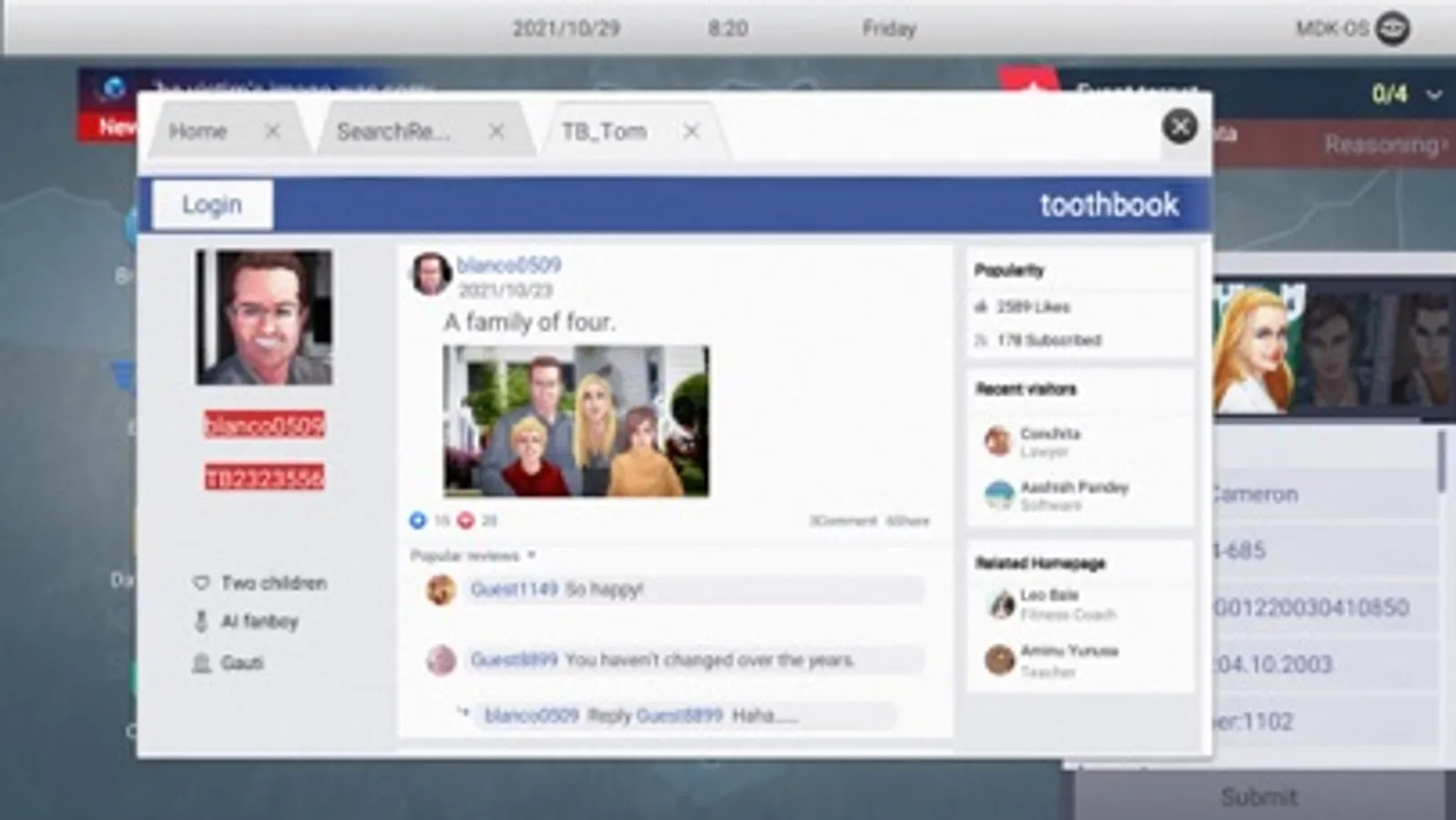
◆Picture Analysis: You can get valuable information and relevant clues from pictures.
More advanced hacking methods will be unlocked later!
We want to reveal the profound themes behind the stories with wonderful plots and gamification. And let players pay more attention to Cyber Violence and Privacy Breaches.
[Contents]
◆Chapter I: Death of a Programmer
The CEO of a company committed suicide by jumping off a building, and claimed that he was extorted tens of millions by his wife. While his wife posted photos of domestic violence on social networks. Who is lying?
◆Chapter II: Invisible Eyes
The indecent video of the female college student went viral on the Internet. At this moment, she was already socially dead. Who is the initiator? Who should protect the safety of women?
◆Chapter III: The Evidence Vanishes
The student council president, who is both excellent in character and study, suddenly disappeared. The bullying incident made the case more complicated. Who is the murderer and who is the victim?
◆Chapter IV: The Price of Humiliation
The female singer has been exposed again! Threatening letters, hype, the suicide of former girl group members... The Internet has set off a public opinion carnival again!
◆Chapter V: Immortal Code
When the society is in madness, are you willing to join the Immortal Code to obtain true love and immortality?
◆DLC: Home Sweet Home
Behind this seemingly sweet and happy family, everyone has their own secrets, what is the truth hidden behind?!
◆DLC: Hello World!
Senior researcher of Titan Dr. Lucrezia died in a terrible car accident on the spot, but the fellow Benjamin took escape from death. But he did not realize that he was about to be involved in a huge conspiracy…
[Features]
◆Highly Immersive: Gamers play as a hacker in the game, accepts the commission of the company, and solve dangerous incidents.
◆Rich Gameplay: There are lots of features of Social Engineering in the game, which is including Detecting, Tracking, Puzzles-Solving, Destroying and Hacking etc..
◆Wonderful Plots: Each chapter in the game will reflect a current hot social topic, such as: Sneak Shot, Cyber Violence, School Bullying, etc...
◆Multiple Roles: There are many different roles in this game with a flash of personality. Their stories would be dug by yourself.
◆Fully Dubbing: All the characters in the game have their own voice actors that make the game experience more immersive.
◆Original Music: There are some original songs in the game, and the lyrics and vocals are all completed by the studio.
[Gameplay]
◆Web Search: You should collect basic information about the targets through the Internet search.
◆Database: You can use the database to get deep information about targets.
◆Crack: You would get passwords based on the obtained target's information, and use it to log in to accounts of different platforms.
◆Chat: The exciting thing is that you need to chat with targets by disguise and use the information to get the trust of the target.
◆Phishing: You can send phishing links to hack the targets' hardware devices, and get private information.
◆Picture Analysis: You can get valuable information and relevant clues from pictures.
More advanced hacking methods will be unlocked later!