About Pass - Password Generator
Pass is a simple, reliable and secure unique password generator.
It is very easy to generate and recover passwords on any ipad or iphone device knowing only the master password, login and service name. You don't need to sync between devices, you only need the same master password.
How it works
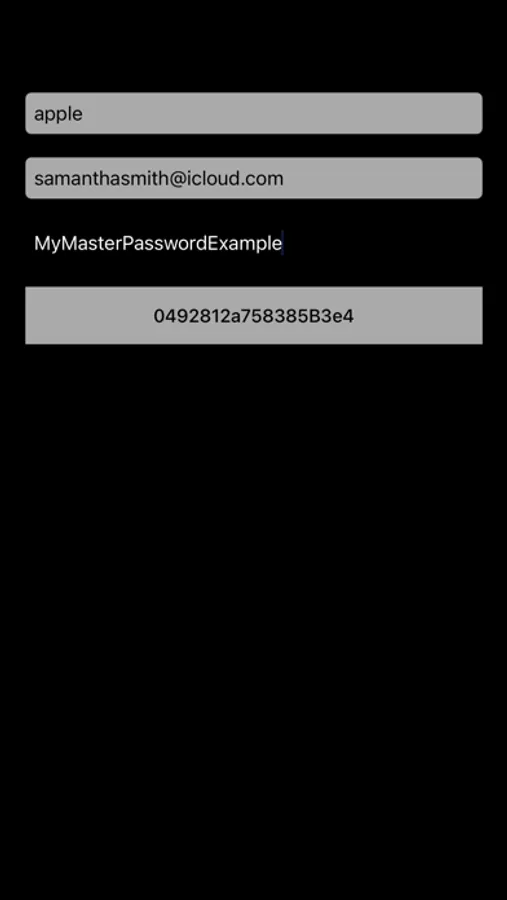
You fill in the fields (for example, let's create a password for the Apple ID)
apple
yourappleid@icloud.com
yourmasterpassword
And done
Just click on the button with the password and it will be copied to the clipboard.
App not using internet, and can't send inforomation somewhere. And it means that information cannot be stolen.
Thanks to a simple and reliable system, your passwords will always be available to you. Just take another iphone/ipad. Install Pass app and enter Master Password, Login and Service name and get your password again. No Sync needed.
To generate a password, the program uses a multi-stage mechanism for generating encryption hashes in various sequences, which in turn depend on the original data.
You can independently check the reliability of the encryption method on such online decryption services as cmd5.ru, crackstation.com, hashcracking.ru
It is very easy to generate and recover passwords on any ipad or iphone device knowing only the master password, login and service name. You don't need to sync between devices, you only need the same master password.
How it works
You fill in the fields (for example, let's create a password for the Apple ID)
apple
yourappleid@icloud.com
yourmasterpassword
And done
Just click on the button with the password and it will be copied to the clipboard.
App not using internet, and can't send inforomation somewhere. And it means that information cannot be stolen.
Thanks to a simple and reliable system, your passwords will always be available to you. Just take another iphone/ipad. Install Pass app and enter Master Password, Login and Service name and get your password again. No Sync needed.
To generate a password, the program uses a multi-stage mechanism for generating encryption hashes in various sequences, which in turn depend on the original data.
You can independently check the reliability of the encryption method on such online decryption services as cmd5.ru, crackstation.com, hashcracking.ru