About IBM Security Verify Request
IBM Security Verify Request provides an interface for the Identity products - IBM Security Verify Governance (ISVG) as well as Identity Manager (IM), which is a component of IBM Security Verify Governance. It enables ISVG or IM users to act on access request approvals or manage passwords while on the move.
IBM Security Verify Request validates your identity with your fingerprint or PIN that's already configured on your device, for subsequent access to the app. (Only for ISVG)
Features:
• MDM (Mobile Device Management) Support
• QR Code based on-boarding support. (Only for ISVG)
• Access using TouchID or PIN. (Only for ISVG)
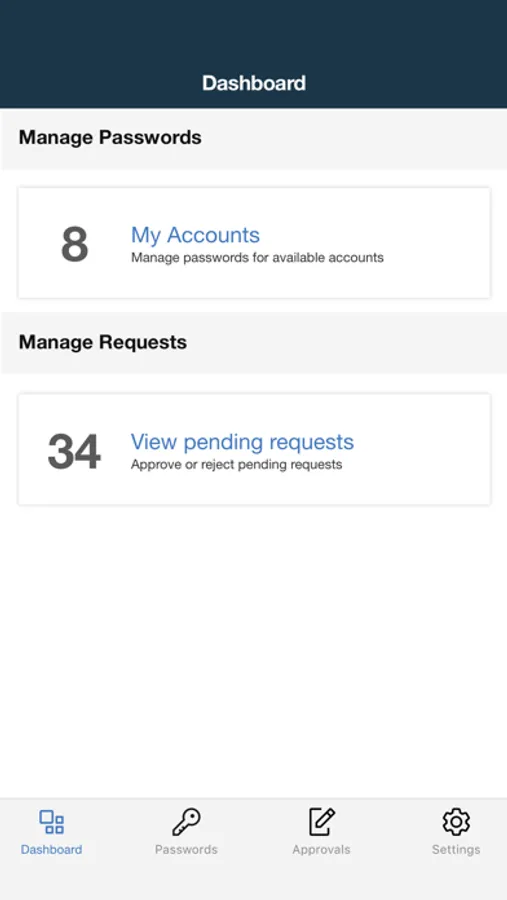
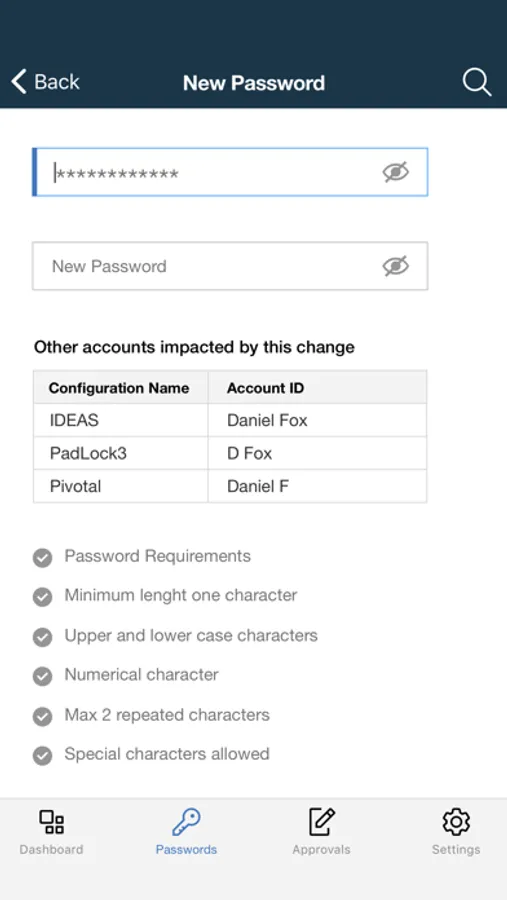
• Manage Password, where employees can change their passwords by providing old and new password.
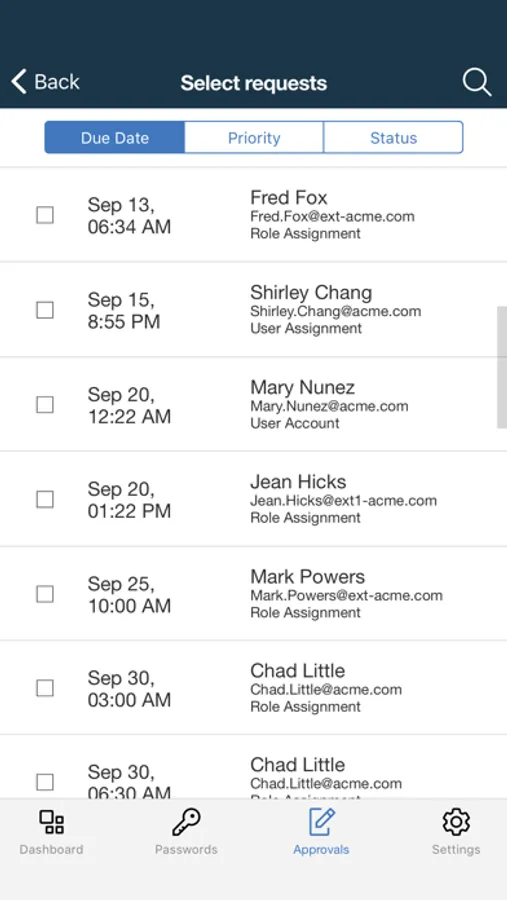
• Manage Approvals, where managers can search, view, approve, reject or redirect pending access requests.
• Forgot Password: Identity Manager (IM) users, can reset their login password, in case they have forgotten it and have legit permissions to do so, as set by the server administrator.
• Logging capabilities
• Act as delegate, where user can act as a delegate for another user and perform actions on tasks on behalf of the delegator user.
• Force password change, when enabled by admin, user is prompted to change the password the next time he logs in.
IBM Security Verify Request validates your identity with your fingerprint or PIN that's already configured on your device, for subsequent access to the app. (Only for ISVG)
Features:
• MDM (Mobile Device Management) Support
• QR Code based on-boarding support. (Only for ISVG)
• Access using TouchID or PIN. (Only for ISVG)
• Manage Password, where employees can change their passwords by providing old and new password.
• Manage Approvals, where managers can search, view, approve, reject or redirect pending access requests.
• Forgot Password: Identity Manager (IM) users, can reset their login password, in case they have forgotten it and have legit permissions to do so, as set by the server administrator.
• Logging capabilities
• Act as delegate, where user can act as a delegate for another user and perform actions on tasks on behalf of the delegator user.
• Force password change, when enabled by admin, user is prompted to change the password the next time he logs in.