About ElIoT Pro
Make your IoT network more secure than ever with ELIoT Pro.
ELIoT Pro eliminates one of the major threats to cybersecurity - the need for passwords between people, machines and devices - to provide complete protection to IoT users, devices and data.
To enable Human-to-Machine logins, ELIoT Pro deploys one-time token technology between your user’s Smartphone and a given IoT device. Lightweight Encryption works as ELIoT Pro’s Machine-to-Machine component and ensures that IoT data
is fully encrypted and sent only to authorized devices.
ELIoT Pro is the most complete end-to-end cybersecurity solution, ensuring your IoT
network are truly protected.
It’s time to take your IoT cybersecurity to the next level with ELIoT Pro.
Why ELIoT Pro?
IoT devices and networks currently suffer from a lack of security leaving them
vulnerable to a wide range of cyberattacks. Whether its rogue nations, thieves or
terrorists’ attacking vulnerable networks, cybercrime is a multi-trillion dollar global
threat. IoT devices when hacked by cybercriminals can create devastating financial
and reputational damage, and may even endanger human lives.
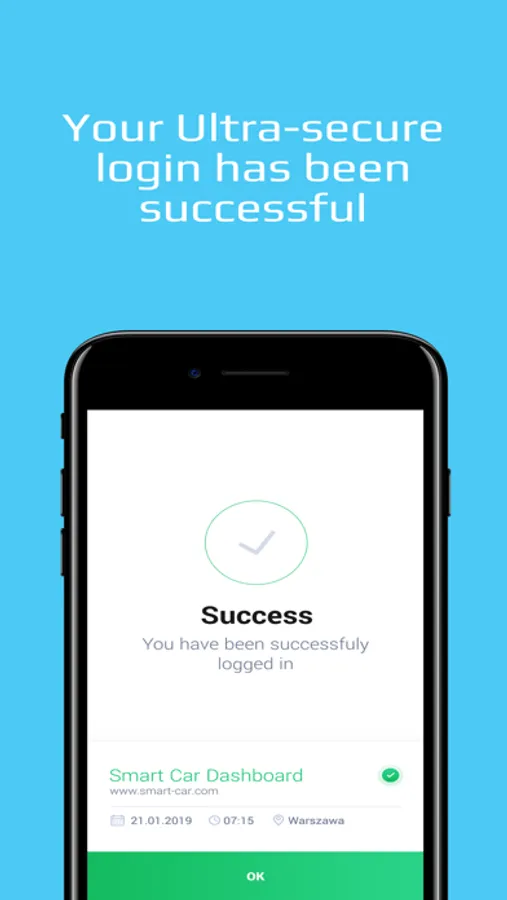
With ELIoT Pro, you will no longer have to worry about cybercrime, knowing that
your IoT users, devices and data are ultra-secure.
COMPLETE IoT SECURITY
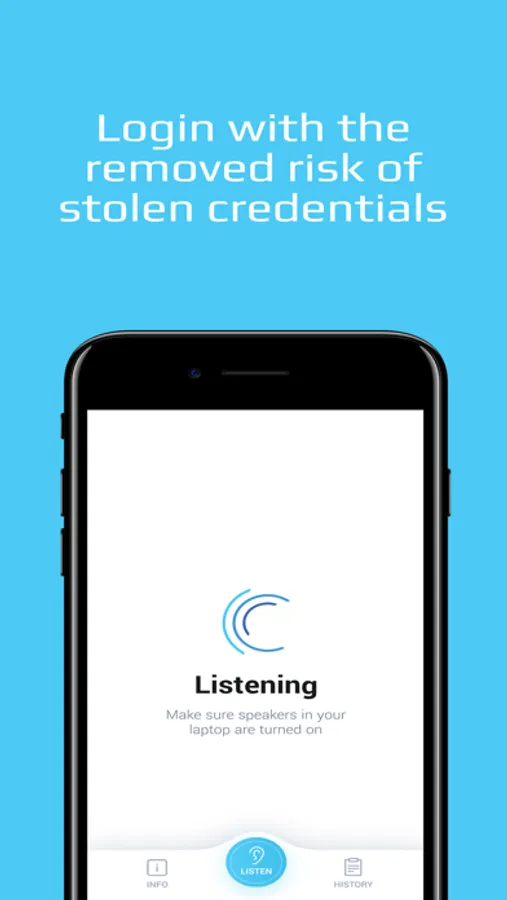
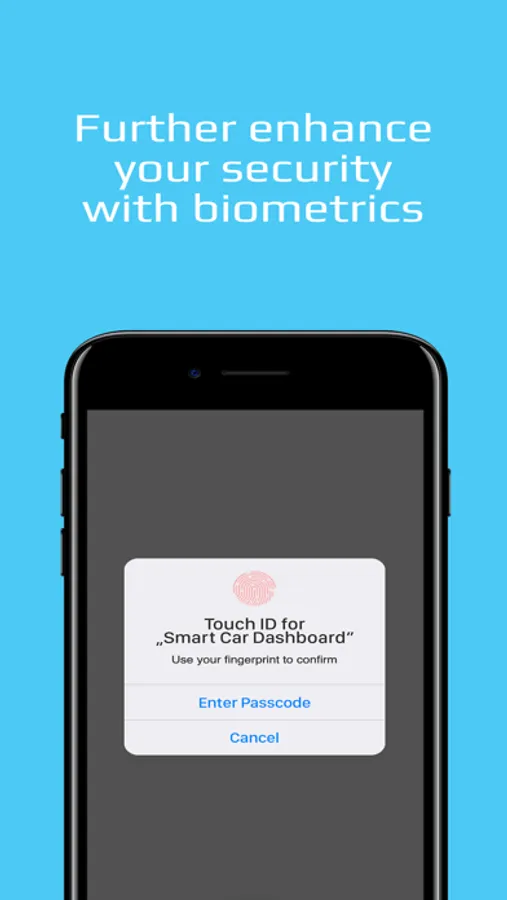
No more passwords or old-fashioned logins means your users’ credentials
can never be stolen. And by eliminating passwords on your connected
devices and machines too, there is nothing for hackers to steal and no way to
gain access.
PROTECT SIMPLE DEVICES
Your IoT devices have different levels of computing power. And our
lightweight encryption requires lower computing power and memory than any
encryption system today – making it work on even the simplest IoT devices.
EASY INSTALL
Whether you prefer cloud-based, on-premise or a hybrid model, it’s easy to
set up and install with API functionality, an SDK, and a white-label option also
available.
VOICE CAPABILITY
Our Smartphone-based user login with sound technology means we provide a
fully secure user authentication mechanism for voice-controlled environments
like Alexa, Google Home, or Siri.
SELF-HEALING
Our AI engine creates an adaptive, self-healing IoT environment to anticipate
system failures, identify attacks, and automatically react.
ELIoT Pro eliminates one of the major threats to cybersecurity - the need for passwords between people, machines and devices - to provide complete protection to IoT users, devices and data.
To enable Human-to-Machine logins, ELIoT Pro deploys one-time token technology between your user’s Smartphone and a given IoT device. Lightweight Encryption works as ELIoT Pro’s Machine-to-Machine component and ensures that IoT data
is fully encrypted and sent only to authorized devices.
ELIoT Pro is the most complete end-to-end cybersecurity solution, ensuring your IoT
network are truly protected.
It’s time to take your IoT cybersecurity to the next level with ELIoT Pro.
Why ELIoT Pro?
IoT devices and networks currently suffer from a lack of security leaving them
vulnerable to a wide range of cyberattacks. Whether its rogue nations, thieves or
terrorists’ attacking vulnerable networks, cybercrime is a multi-trillion dollar global
threat. IoT devices when hacked by cybercriminals can create devastating financial
and reputational damage, and may even endanger human lives.
With ELIoT Pro, you will no longer have to worry about cybercrime, knowing that
your IoT users, devices and data are ultra-secure.
COMPLETE IoT SECURITY
No more passwords or old-fashioned logins means your users’ credentials
can never be stolen. And by eliminating passwords on your connected
devices and machines too, there is nothing for hackers to steal and no way to
gain access.
PROTECT SIMPLE DEVICES
Your IoT devices have different levels of computing power. And our
lightweight encryption requires lower computing power and memory than any
encryption system today – making it work on even the simplest IoT devices.
EASY INSTALL
Whether you prefer cloud-based, on-premise or a hybrid model, it’s easy to
set up and install with API functionality, an SDK, and a white-label option also
available.
VOICE CAPABILITY
Our Smartphone-based user login with sound technology means we provide a
fully secure user authentication mechanism for voice-controlled environments
like Alexa, Google Home, or Siri.
SELF-HEALING
Our AI engine creates an adaptive, self-healing IoT environment to anticipate
system failures, identify attacks, and automatically react.